Secrecy Through Electronics
|
|
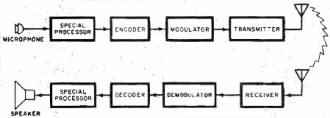
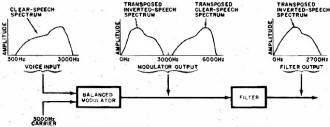
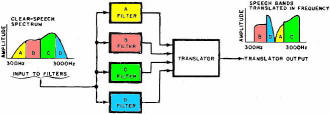
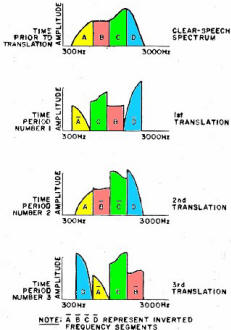
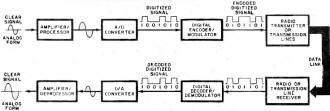
Secure communications has been a concern to governments, corporations, and even private individuals since the beginning of time. Lives and fortunes depend upon being able to guarantee confidentiality in data and messaging. Guarded meeting rooms, secret couriers, and trusted comrades were the earliest forms of secure communications when word of mouth and written messages were the only means available. Once electronic transmission and reception came onto the scene, new methods were needed to help protect message content since access to the signaling media was often as simple as tapping into a telegraph or telephone wire or tuning a wireless receiver to the frequency of interest. A need for real-time encoding and decoding of messages in order to support convenient conversation required the development of not just sophisticated and efficient cryptographic techniques, but also high speed hardware and, eventually, software. The entire story of secure communications would fill volumes. This article from a 1974 issue of Popular Electronics magazine provides a layman's introduction to the topic, and then an accompanying scrambler / unscrambler article entitled, "Enjoy Private Messages with a Voice Scrambler" provides a simple project for building your own crypto set. In the last few days Google announced that it had successfully demonstrated a 53-qubit quantum computer system that can process cryptographic sequences in mere seconds that would require normal computers centuries to do. Some day our progeny will roll their eyes and laugh at the thought of a mere 53-qubit computer being regarded as a major breakthrough. Secrecy Through Electronics - The art and techniques of security in communications today By Clay Tatom Motorola Inc., Semiconductor Products Div. Fig. 1 - Simplified block diagram of scrambler using radio link, but transmitter and receiver can be direct-coupled. Fig. 2 - Inverters transpose high-frequency components. Not too long ago, "security" meant something very different from what it does today. Now, it is a synonym for "protection" from thefts of anything from real property to communication information. So high is the interest in secure communications that the U.S. Government plans to make all official communications secure by the mid-1980's. Other governments and many industrial and commercial establishments throughout the world are following suit. So too are a number of private citizens who want to preserve the privacy of their communications. The growth of electronic communication since 1940 has revolutionized the secret world of cryptology. Wires and radio waves now, carry unbelievable quantities of communication information at staggering rates. Electronics provides the means of unauthorized and illegal eavesdropping on this information. Some of this eavesdropping is done by specialists with expensive "bugging" equipment, posing a real threat. Much of it is by amateurs, listening in on business, Public Safety, and other "private" radio broadcasts. Radio receivers are readily available for monitoring taxicab, aircraft, and police dispatches. Some police departments might condone "good-citizen" monitoring of their broadcasts since it increases the number of observers on the lookout for stolen cars, fleeing suspects, etc. More often than not, however, they prefer, that private citizens do not listen in. Some communities, in fact, have enacted laws that make it illegal for any but authorized law enforcement personnel to monitor police broadcasts. Security Goes Public Industrial and private secure-communication systems generally employ simpler enciphering techniques than those used by the high level governmental agencies. While these are relatively simple systems today, they would have boggled a cryptanalyst's mind only a few decades ago. Most such systems are electronic, designed to effectively thwart the casual would-be eavesdropper. They are, however, relatively easy to decode if the eavesdropper is willing to spend the money to attack them with sophisticated techniques. Fig. 3 - Bandsplitters divide signal and then recombine. Fig. 4 - Combined bandsplitters split and translate speech frequencies to provide more security than simple systems. Most companies that make secure voice systems use a "scrambler" technique. The scrambler, as its name implies, mixes up (scrambles) the speech portions of the audio-frequency range. Scramblers have the advantage over more secure governmental systems in that they are inexpensive, compact, often require only narrow-bandwidth transmission channels, and offer adequate security for their proposed use. They generally provide several hours of security even against the serious commercial eavesdropper. A generalized block diagram of a speech scrambler is shown in Fig. 1. The operator speaks into the microphone. Following the mike may be special processing circuits like speech compressors, delta-modulation response-curve generators, etc. The processed speech signal then undergoes some form of encoding, analog or digital, in some combination with an electronic "key" whose methodology appears to be random in nature. If an all-digital scheme is used, an analog-to -digital (A/D) converter becomes part of the encoder, while a digital-to-analog (D/A) converter becomes part of the decoder. The encoded signal passes on to a modulator where it is impressed on a carrier or other transmission medium. At the receiving end, the reverse of the process occurs. Encoding Techniques There are basically two types of techniques used for encoding communication signals to secure them against immediate unauthorized decoding by eavesdroppers. They include a variety of analog and digital approaches. Simple-Speech Inverters: Inverters transpose the high-frequency components of the speech signal to low frequencies. This is done before carrier modulation in radio transmitters or before line transmission in telephone systems. A stable audio oscillator operating at about 3000 Hz can feed a balanced modulator along with the voice signal. The lower sideband generated reflects the mirror image of the speech frequencies.(See Fig. 2.) Bandsplitters: Bandsplitters divide the audio speech frequencies into several ranges, permitting the narrow frequency bands to be rearranged as shown in Fig. 3. Bandsplitting is usually accomplished with the aid of narrow-bandpass filters. The outputs of the filters are mixed or shifted in frequency, then added together so that some ranges are translated in frequency. Combined Bandsplitters: Combination techniques offer added security to the basic bandsplitting approach. Not only can the speech frequencies be split and translated, but some can be inverted as well. The order in which the frequency ranges are recombined can also be changed with time as illustrated in Fig. 4. (Some manufacturers term these "rolling-code" bandsplitters and rearrange the frequency band order several times.) Using more bands makes this approach more difficult to decode; and changing the band-sequence a greater number of times per second makes the system more secure. Penalties of the combined-bandsplitting technique are that the recovered speech begins to sound unnatural when frequency slices increase in number and closer synchronization tolerances must be exercised during band rearrangement. Masking Techniques: Constant audio tones, or coded sequences of tones, are often used with bandsplítting and inversion. The tones, subtracted from the signal during recovery and decoding, can be higher than or the same level as the intelligence signal (voice). If they are higher in level, they can reduce range since they make up much of the sideband energy and, hence, reduce the system's overall signal-to-noise (S/N) ratio. Pseudo-random noise generators can also be used in masking techniques. In practice, the human ear and brain provide such selective filtering that in a system supposedly offering about 400 word codes, only 10 or 12 might be all that are really different to a listener. To someone trained in decrypting such systems, often 50 percent bf the information can be extracted in just a few attempts. Even inverted speech becomes intelligible after training. Some languages are often less affected than others by these conventional scrambling techniques. The above mentioned analog encoding techniques have been discussed with reference to voice signals. However, the same techniques can also be used to scramble data. They can be applied after the data is fed into a modem and converted to a series of audio tones for analog transmission. The most sophisticated, expensive, and secure communication systems are digital. In Fig. 5 is shown a typical digital voice-encoding system. At the heart of the security system are the digital encoder/modulator and its counterpart, the decoder/demodulator. These systems combine some digital key with the digitized signal. In many cases, synchronization requirements can be very stringent. The complexity of the digital encoder varies with the degree of security required. Requirements can range from several years security for high-level governmental communications to a few hours or minutes in the field for military tactical operations. A few hours to several days generally suffice for most industrial and commercial activities. The main disadvantages of digital encoding systems are their high cost, large size, and often, greater bandwidth requirements on the transmission links. On the other hand, such systems provide the highest degree of security available for both voice and data. There is also high flexibility in transmission routing and voice, and data links are often compatible. Most government, systems are classified. Hence, no details of their design or operating principles can be provided here. There is a book, however, The Codebreakers by David Kahn, that goes into some detail on the subject, using material from unclassified sources. Cryptanalysis Most industrial spies record an intercepted message on tape and then apply successive demodulation and/or decrypting techniques. Several switched filter banks and balanced modulators are used to decrypt band splitting, while the eavesdropper uses his ear and brain to tell him when he is getting close to his goal. Computers are no doubt used in digital cryptanalysis. They make a series of possible solutions of transpositions and substitutions easy to print out. Also, it is easy for the computer to look for patterns in given languages by determining which symbols occur most often. In straight English text, the frequencies of occurrence of alphabet letters are as follows:
(In any average piece of English writing, letters are found in a standard ratio that varies only slightly from message to message. If the message is long enough, it can be decoded by use of letter frequercy tables. Since e is the most common letter, all other letters are given in relation to it. Hence, if e occurs 1000 times, the other letters will be found to have the approximate ratios given above.) Future Trends As one might expect, all of the communications security equipment currently being designed relies heavily on solid-state electronics. Most of the industrial and commercial systems still employ discrete components, but the government is forging ahead with more integrated circuits. The trend is toward more and more sophisticated systems, with the demand for tighter security increasing, as is the technical competence of the would-be eavesdropper. Non-government users are beginning to look at digital techniques. As lower prices and new IC's to perform digital-to-analog and analog-to-digital conversions become widespread, this trend toward digital systems will undoubtedly accelerate. The Motorola MC1408 D/A converter IC is representative of the new integrated circuits on the market today. A practical encoder would combine an MC1408 with other logic and/or speech-processing circuits to give the particular results desired. Most filtering and speech processing is accomplished with the aid of operational-amplifier IC's. The encoding and decoding circuits themselves can employ many of the standard shift registers, read-only memories ('ROM's), random-access memories (RAM's), and gate arrays already in common use. These types of IC's are available in today's popular logic families. At one time, governments were the only users of secure communication systems. Later, commercial organizations became security-conscious in their efforts to thwart industrial espionage. Now, the private citizen, concerned over bugging-operations and other invasions of privacy, has taken up the security banner. For him, the voice scrambler seems made to order.
Posted September 23, 2019 |
|